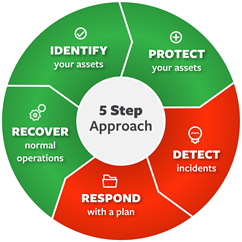
Endpoint Detection and Response (EDR) solutions have become a necessary component of each organization’s security architecture and look to assist the Security Operations Center’s (SOC) ability to meet steps 3 and 4 of the National Institute of Standards and Technology (NIST) Cyber Security Framework:
- Identify
- Protect
- Detect
- Response
- Recover
Yet, when you look at most of the literature for these solutions, they only market the ability to detect malicious or anomalous events in real time. Detection is absolutely a core ingredient, but what about response? What can these solutions do to enable a security analyst to efficiently conduct an incident response?
To answer this question, it’s important to look at what a security analyst needs to accomplish during an incident response.
First, the analyst receives an alert in the EDR or Security Information and Event Management (SIEM). This alert notifies the analyst that their automated software detected a potentially malicious incident that needs to be analyzed.
To do this, the analyst must sort through all of the collected data on the endpoint to determine if the incident was malicious or whether it was a false positive. In order to accomplish this effectively, an analyst needs to get immediate access to the step-by-step actions of the offending user ID, IP address, or service that triggered the alert. This provides a timeline of actions that enables the analyst to make a quick determination on whether it needs to be escalated or was a false positive that can be solved.
Organizations need to leverage software solutions to increase the efficiency of their analysts, making each individual able to accomplish the work of multiple
A good EDR solution provides the analyst a framework to quickly visualize the triggered timeline and efficiently analyze each alert. In the growing demand for cyber security talent, organizations need to leverage software solutions to increase the efficiency of their analysts, making each individual able to accomplish the work of multiple resources. 1 The investment in quality solutions will end up reducing the required manpower for a SOC and will save an organization on critically short resources.2
So why is establishing this timeline such a challenge for most organizations? Most of it comes down to the quality of data that reaches the SIEM. As regulations continue to put immediate pressure on organizations, they find themselves in a check-the-box situation where they find the first method possible that enables them to store data like failed logins, file activity monitoring, or privileged users before their upcoming audit. The data will often be ingested in a SIEM or data lake where vendors claim their solution will be able to quickly and effectively sort through stored data. Unfortunately, most of the data is sent and stored without the greater understanding of incident response and will lack core components for establishing a timeline.
This is especially true on the mainframe because the Server Message Facility (SMF) that captures event data on the z/OS wasn’t designed to catch hacker activity. This means that those critical SMF records which security analysts would have to use lack critical information that they would need to filter on. Organizations may feel secure, having just passed an audit, but will quickly find their actual capability for conducting required cyber security practices is limited because incident response will resemble a search for a needle in a haystack.
The solution: BMC AMI Security
BMC AMI Security can help. To facilitate incident response, BMC AMI Security enriches each captured SMF record with relevant information like user IDs and IP addresses that enable security analysts to filter on the alerted trigger and establish the critical timeline which enables them to efficiently respond to the incident. This is enabled through the lightweight agent that runs on each logical partition which can access the key details from the operating system memory and add it as a field before sending the event off to the SIEM or data lake. Now, analysts can build a holistic timeline in seconds instead of coming through all events in a certain time window. This will significantly enhance the capability of each security analyst in the SOC as they leveraged the intelligence of the software that was built with true automated mainframe security in mind.
If you feel secure in your current solutions, then you should begin the practice of testing your defensive posture through cybersecurity simulations. These simulations will model a true cyber security incident to test your organizations ability to detect and respond to real threats. Just like military exercises, rehearsals are a core component to testing, training, and improving your defenses. In today’s age where a criminal can rent Ransomware as a Service3 and can begin having catastrophic impacts on an organization is as little as 18 minutes from first infection4 this can be the difference between losing the indispensable data that runs on the mainframe or responding to a threat in time.
If you’d like to learn more about mainframe security or how BMC AMI Security can help you detect and respond to very real mainframe cyber risks then please contact your account manager or click here to sign-up for a free trial of BMC AMI Security.
1 https://cybersecurityventures.com/jobs/ ↩
2 https://www.gartner.com/smarterwithgartner/solve-the-cybersecurity-talent-shortage/ ↩
3 https://nakedsecurity.sophos.com/2017/12/13/5-ransomware-as-a-service-raas-kits-sophoslabs-investigates/ ↩
4 https://www.zdnet.com/article/you-have-around-20-minutes-to-contain-a-russian-apt-attack/ ↩
Mitigating Mainframe Security Risks with Endpoint Detection and Response
These postings are my own and do not necessarily represent BMC's position, strategies, or opinion.
See an error or have a suggestion? Please let us know by emailing blogs@bmc.com.







